
Next-Generation Malware Analysis and Threat Intelligence
Built for Enterprise SOCs and Security Companies
Detect zero-day malware with few false positives, and when needed – get detailed actionable intelligence on malware.
GET TO KNOW OUR PRODUCTS
Deep View Intel
Look up our vast database with file hashes or URLs (websites) to get a malicious/benign verdict and other attributes.
+ VAST DATABASE:
We ingest more than a million files and URLs per day into our database, leading to a large and valuable database.
+ ACCURATE:
Powered by zero-day verdicts from our Scanner product.
+ SCALABLE:
Look up tens of millions or more hashes or URLs per day, with latency < 0.1 seconds per lookup.
Security and Software Companies
OEM DeepView Intel to integrate into your software product to detect malicious files and websites, without the need for full files or websites.
Enterprise
SOCs
Use DeepView Intel to triage files quickly, reducing alert fatigue by flagging false positives from Endpoint and Network Security tools, without the need for full files or websites.
Deep View Scanner
For quick malicious/benign verdicts on any number of files or websites.
+ ACCURATE:
Industry-leading detection rate that beats AV tools, with few false positives.
+ SCALABLE & AFFORDABLE:
Scales to millions of files per day at an affordable price.

Security and Software Companies
OEM the DeepView Scanner to integrate into your software product to detect malicious files and websites.

Enterprise
SOCs
Use the Scanner to triage files quickly from you SOAR platform – reducing alert fatigue by flagging false positives from Endpoint and Network Security tools.
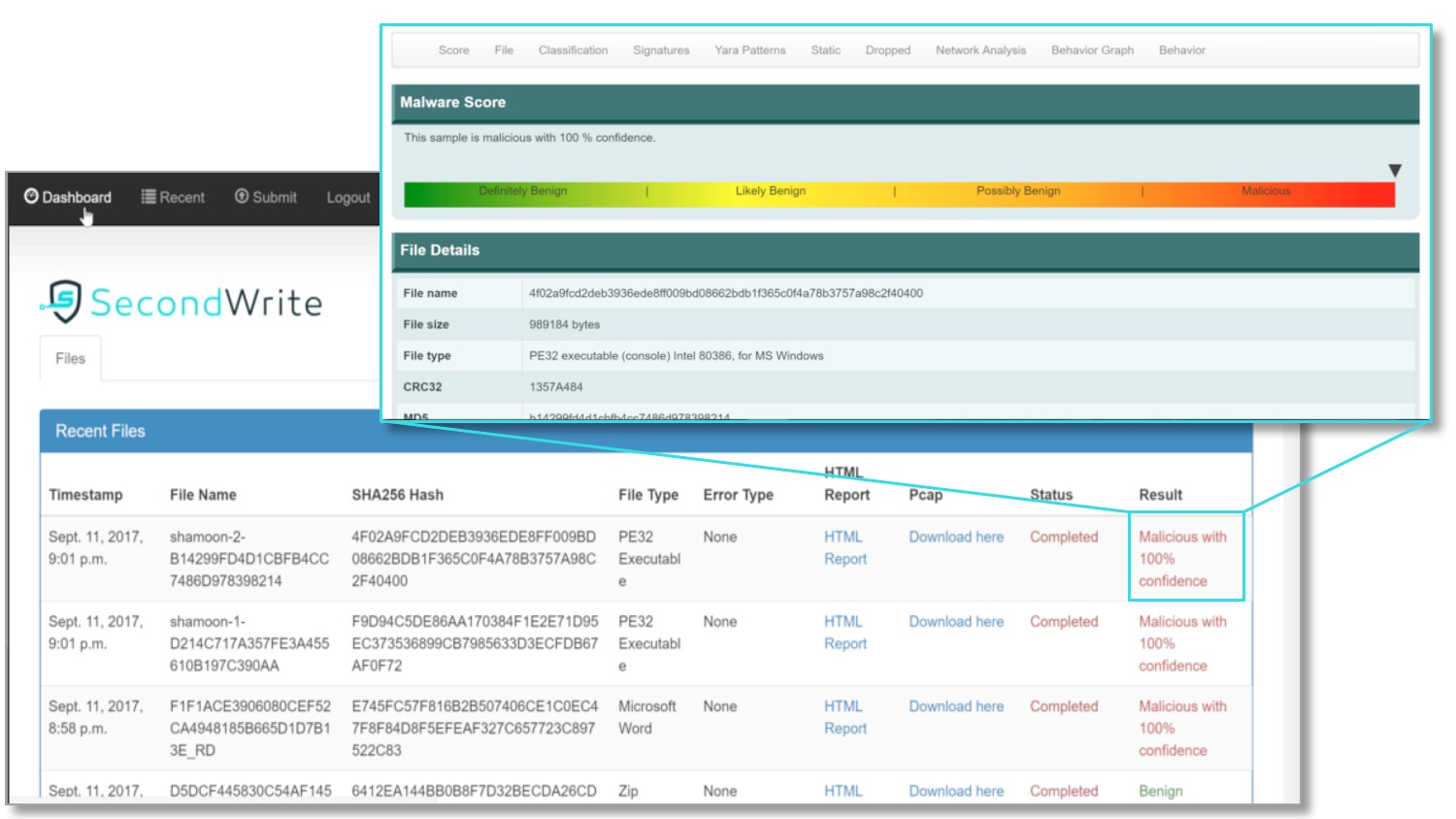
Deep View Sandbox
Get actionable intelligence with a detailed JSON and HTML report for each file or website submitted.
+ DETAILED:
Contains a wealth of information including dynamic Indicators of Compromise (IOC’s), YARA patterns, MITRE ATT&CK classification, malware classification, file system behavior, and network behavior.
+ REVEALS EVASIVE CODE:
Uncovers behaviors of evasive malware by using our patented Forced-Code Execution (FCE) technology.

Security and Software Companies
OEM the DeepView Sandbox to enrich your threat intelligence, provide customers malware reports on demand, or use for threat hunting.
Enterprise
SOCs
Use the DeepView Sandbox to accelerate Reverse Engineering, and/or for attack damage assessment, remediation and response.
End-Point & Network Security Vendors (IDS/HIDS/NIDS)
Get definitive verdicts on “unknowns” or “suspicious” files & URLs
Security Analysts / Threat Hunters
Get a jumpstart with details on observed malicious behavior*
MSSPs/SOARs
Reduce alert fatigue with highly accurate verdicts & API integration
Enterprise SOCs/NOCs
Leverage your Level 1 security analysis with attack specifics in reports
Threat Intelligence Providers
Get definitive verdicts plus detailed attack data to enhance your threat intel
*malicious behavior: dropped/read/written files, network traffic, IPs/DNSs, called/executed code, sniffed/scanned user interactions, registry changes
Whether It’s 10… 100… 1,000… 10,000… 1,000,000 Files,
the DeepView Suite of Products Analyze Many Files and Websites in Parallel
1. QUICK SEE
Use Second Write's web portal to access pre-loaded Deep View Sandbox reports for a selection of real malware files.

2. FAST EVAL
Use SecondWrite’s web portal to submit your own files or URLs to the Deep View Scanner and Sandbox, or file hashes and URLs to DeepView Intel, and view results*.
.

3. FULL PILOT
Use SecondWrite’s REST API to submit files or URLs to Scanner or Sandbox, or file hashes or URLs to Intel, and access their results.
“We are detecting 100’s of malware files per day with DeepView Sandbox; these are typically are zero-day or evasive techniques that our other detection methods cannot definitively resolve.”