End-Point & Network Security Vendors (IDS/HIDS/NIDS)
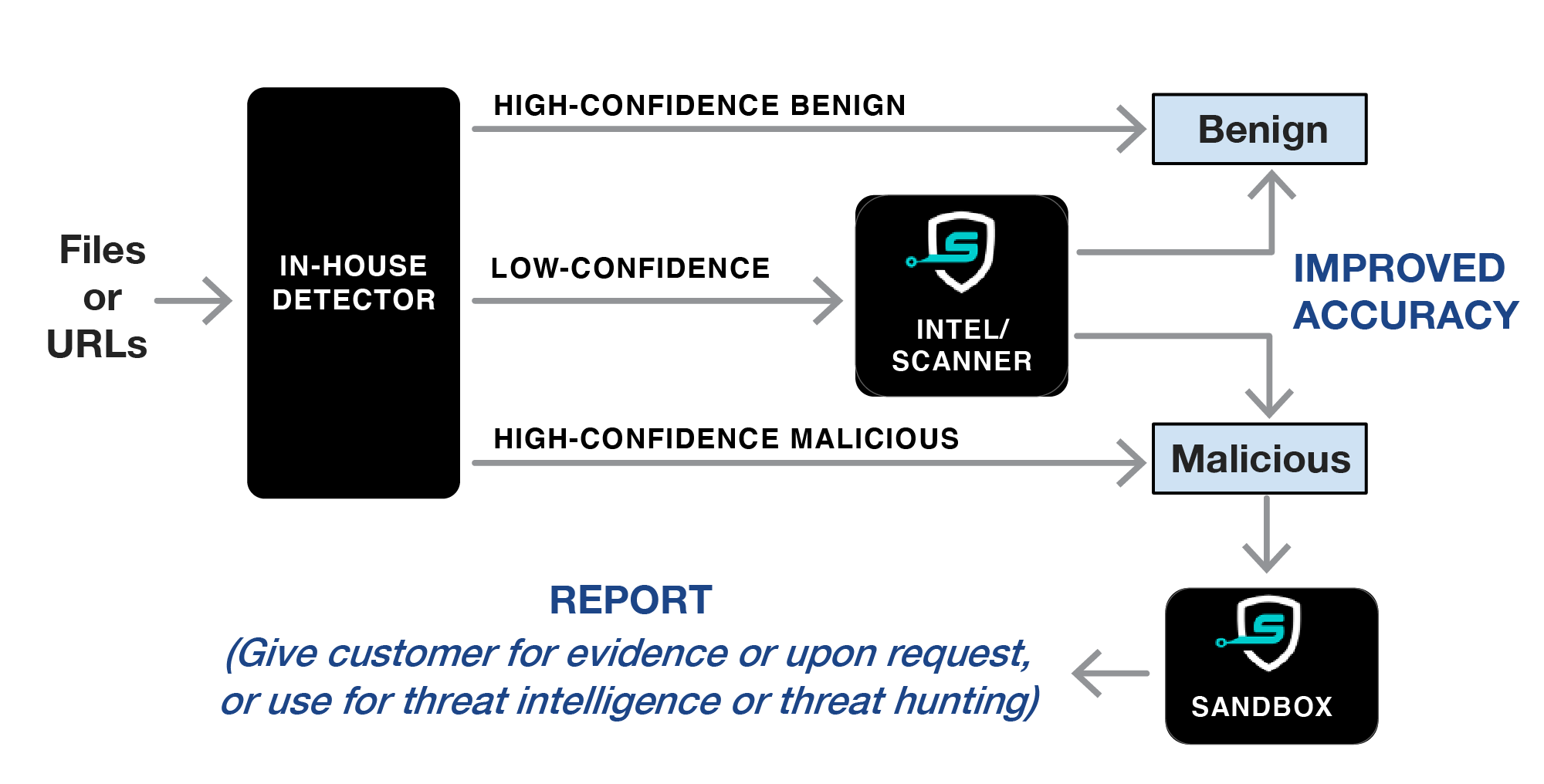
- Analyze “Unknown”/”Suspicious” files or URLs from customers with low-confidence verdicts using SecondWrite Intel and/or Scanner, which does accurate zero-day analysis. This increases malware detection rates and reduces false positives.
- Sandbox report can be used to gain detailed telemetry for file or URL, provide customer evidence for why the file was convicted, or supplement machine learning.
Security Analysts/Threat Hunters

- Use SecondWrite Sandbox to analyze malware and find related threats. Report contains detailed telemetry such as suspicious IOCs, YARA pattern matches, MITRE ATT&CK classification, malware family, dropped files, deleted/written/read files, and domain names and IP addresses connected to.
MSSPs/Enterprise SOCs
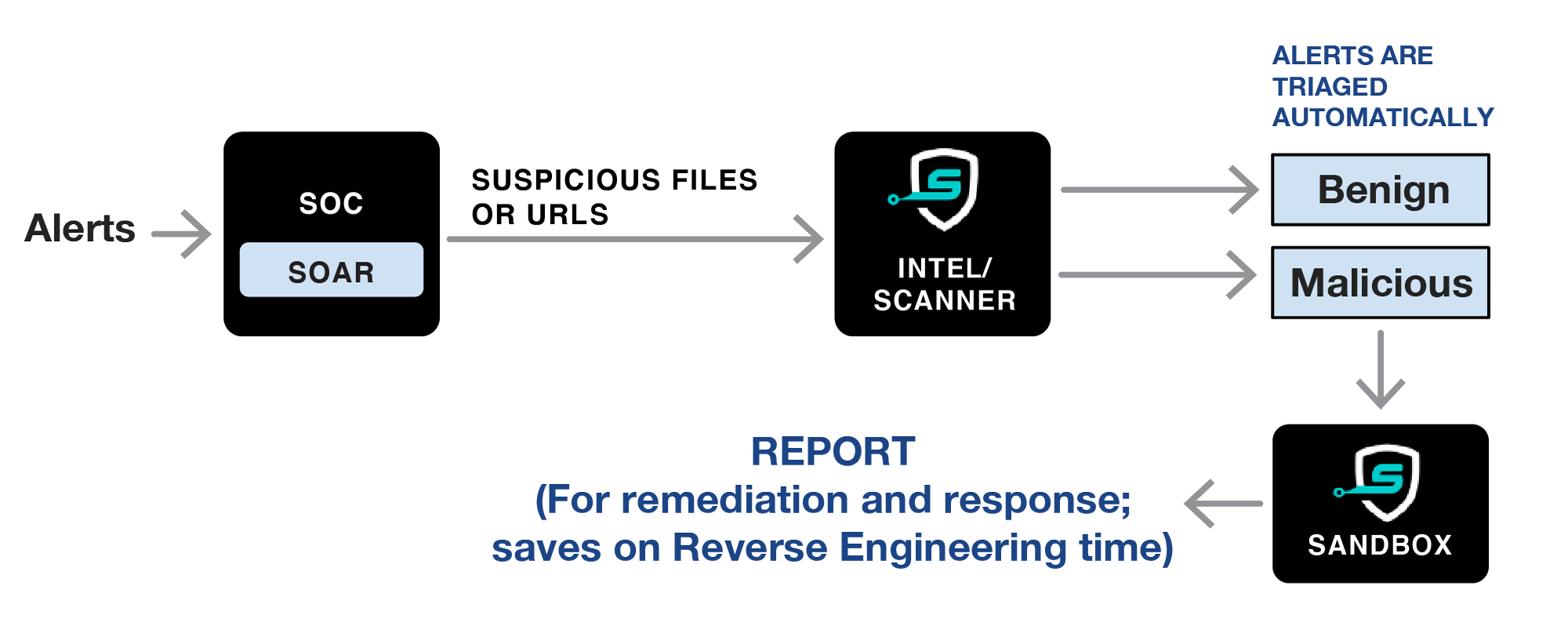
- Reduce alert fatigue: Use Intel and/or Scanner on files or URLs associated with alerts from 3rd party Endpoint and Network tools. Provides quick and accurate 2nd-opinion verdict to accurately and automatically triage alerts. This reduces analyst time, increases malware detection, and reduces false positives.
- Detailed Sandbox report provides a great starting point for reverse-engineering high-interest files and URLs, reducing analyst time for RE.
Threat Intelligence Providers
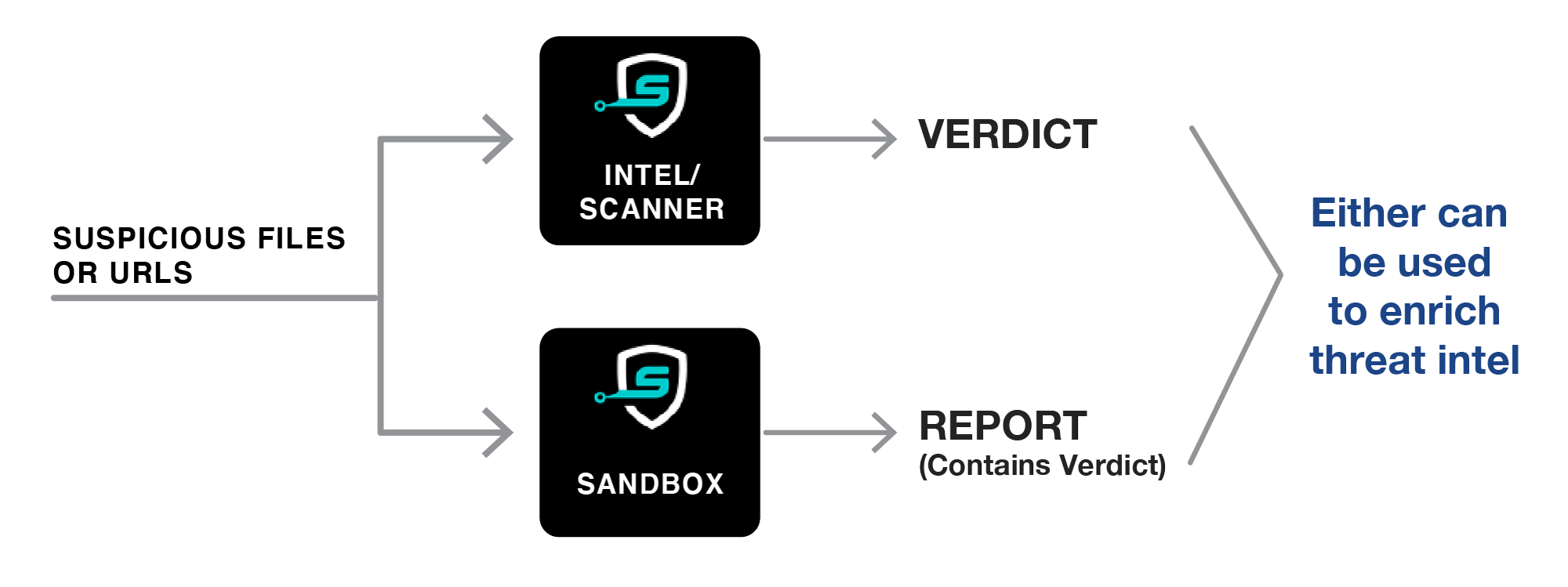
- Enrich your threat intelligence database using the results of our Intel, Scanner or Sandbox on suspicious files or URLs you analyze.