7fbbd075d1c2afb0bda717fde96ae452b104b628348a4454e14f2e3a07828f67 (SHA-256)
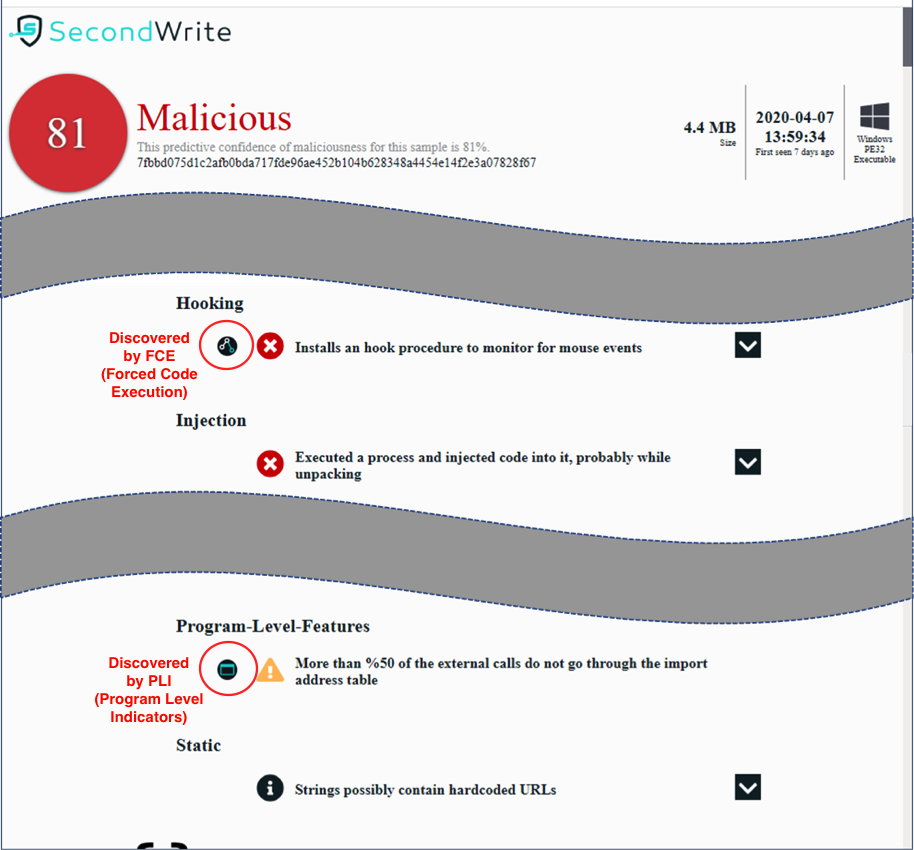
Malicious with 81% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious using our proprietary techniques. At the time of detection, this malware did not appear on many of the leading malware blacklists. A link to the full report is below and some key highlights follow:
Type of Malware: Trojan
– One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
– This executable has a PDB path
– Installs a hook procedure to monitor for mouse events
– Executed a process and injected code into it, probably while unpacking
– Drops a binary and executes it
Evasiveness Indicators:
– Checks whether any human activity is being performed by constantly checking whether the foreground window changed
– Checks for the presence of known devices from debuggers and forensic tools
– Checks the version of Bios, possibly for anti-virtualization
– Detects VMWare through the in instruction feature
– A process attempted to delay the analysis task
Other Compelling Indicators:
– Reads data out of its own binary image
– Allocates read-write-execute memory (usually to unpack itself
– Creates an Alternate Data Stream (ADS)
– More than %50 of the external calls do not go through the import address table
– Attempts to repeatedly call a single API many times in order to delay analysis time
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Software Packing | Defense Evasion |
| Virtualization / Sandbox Evasion | Discovery |
| Remote File Copy | Command and Control |
| Process Injection | Defense Evasion Privilege Escalation |
| NTFS File Attributes | Defense Evasion |
| Credential Dumping | Credential Access |
Selection From The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution,Program Level Indicators, and Automatic Sequence Detection
