The latest ransomware attack on the world has hit at least 65 countries and thousands of computers. Many news reports claim that this is just the beginning of more cyber-attacks to come in the future. This malware is significantly different from previous variants of the Petya ransomware that was active last year and has been named #NotPetya by many. At present the extent of the damage caused by this malware has not been completely accessed. Its victims include many financial institutes, banks, airports and hospitals to name a few.
At SecondWrite, we are developing an advanced malware processing engine (MPE) to detect such advanced and dangerous malware using deep program introspection. We took this malicious sample and analyzed it using our MPE. SecondWrite’s MPE declared it as malicious and also detected several behavioral indicators of compromise (IOCs) from the sample.
The SecondWrite MPE declared the sample to be malicious with very high confidence.
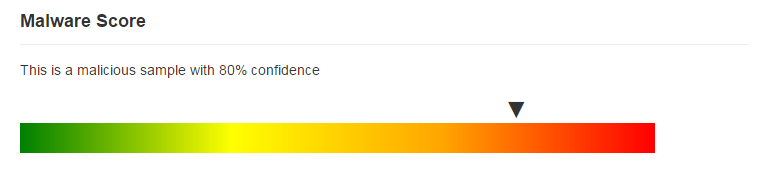
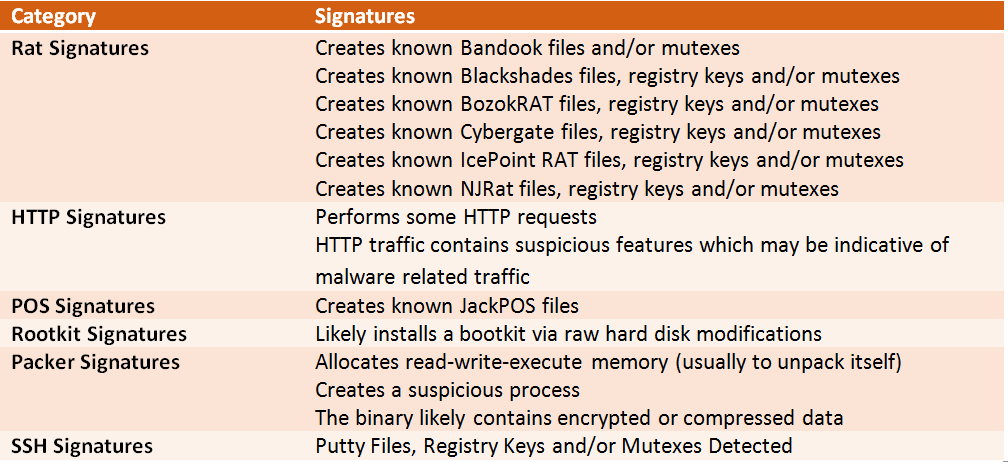
To provide you an insight regarding indicators of compromise that were unearthed, we present a few.
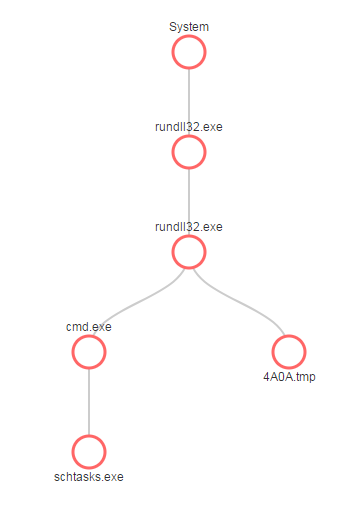
This ransomware works through a Dynamic Loaded Library (DLL). A DLL is dropped to a victim machine and executed to schedule a service for performing the file encryption. Below, we demonstrate this internal behavior of this sample, as captured through SecondWrite MPE:
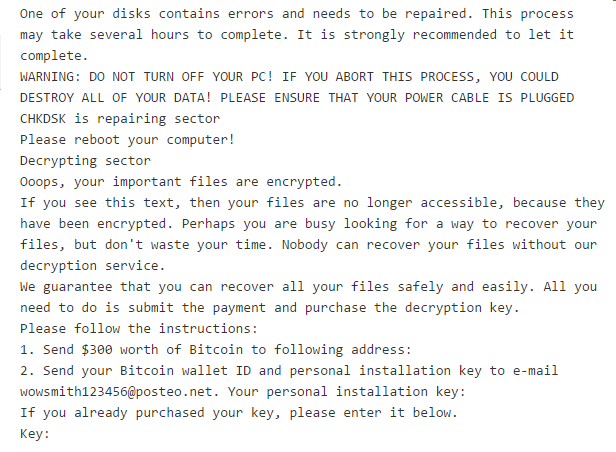
Our static analysis also extracted all the strings present. Here is an interesting one which includes the ransomware demand message.