9c544a7c52553e62951b2aa2b33402c93be09f2f0fdb442f5790bb4d983f0b21 (SHA-256)
Malicious with 82% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious.
DeepView unique and patented methods – specifically in this case, force code execution identified 4 indicators. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow. Those discovered by DeepView proprietary methods are flagged with [FCE] for forced code execution.
Type of Malware: Adware
- [FCE] Installs a browser add-on or extention
- Sniffs keystrokes
- Installs an hook procedure to monitor for mouse events
- This sample modifies many files through suspicious ways, likely a polymorphic virus or a ransomware
Evasiveness Indicators:
- A process created a hidden window
- Attempts to repeatedly call a single API many times in order to delay analysis time
- [FCE] Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available
- Deletes its original binary from disk
Other Compelling Indicators:
- [FCE] Attempts to stop active services
- [FCE] Sample writes a large amount of files (Over 100)
- Creates known Dexter registry keys and/or mutexes
- Network activity contains more than one unique useragent.
- Resolves .RU Russia TLD, Possibly Malicious
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Persistence | Browser Extensions |
| Defense Evasion | Software PackingVirtualization / Sandbox EvasionHidden WindowNTFS File AttributesFile DeletionConnection Proxy |
| Credential Access | Credential Dumping |
| Discovery | Virtualization / Sandbox Evasion |
| Lateral Movement | Remote FIle Copy |
| Command and Control | Remote File CopyConnection Proxy |
Selection from The Report:
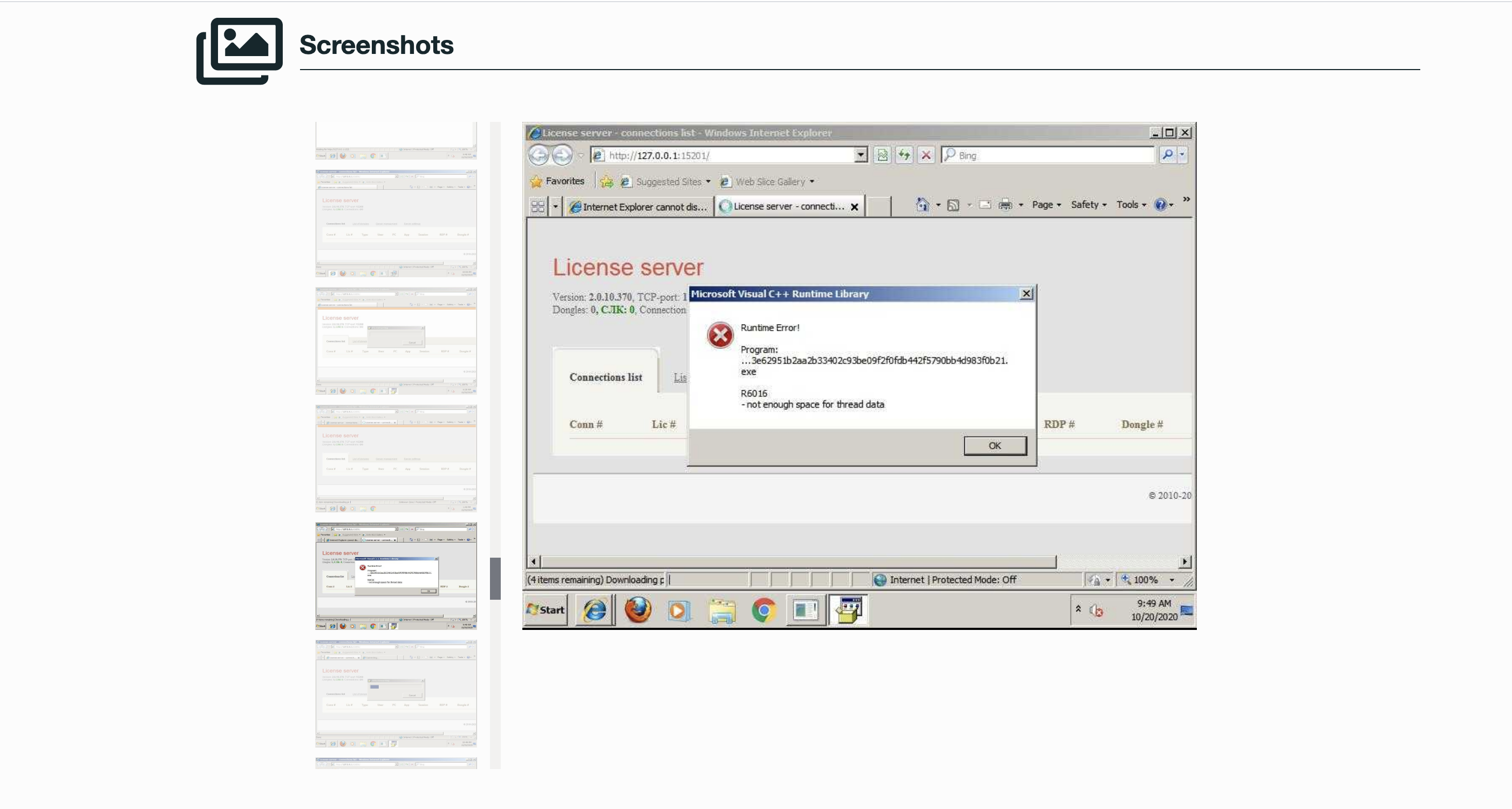
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.
