cbb006846738e71d607714cc3daa16475f04c8e725025a9ba5cbb52785ab959c (SHA-256)
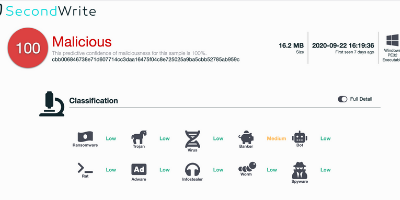
Malicious with 100% Confidence
SecondWrite’s DeepView Sandbox analyzed this file – a Windows PE32 Executable – this week and declared it to be malicious. At the time of its discovery, some malware detection vendors had not identified this file as malicious. DeepView unique and patented methods identified 8 indicators – specifically in this case, force code execution (FCE) and program level indication (PLI). A link to the full report with descriptions and details is below.
Some key highlights and indicators follow.
Type of Malware: Banker
- Attempts to modify browser security settings
- [FCE] Attempts to modify proxy settings
- [FCE] Expresses interest in specific running processes
- [FCE] A process created a hidden window
- [FCE] Sample contacts servers at uncommon ports
Evasiveness Indicators:
- [PLI] Contains obfuscated control-flow to defeat static analysis
- A process attempted to delay the analysis task
- Tries to suspend sandbox threads to prevent logging of malicious activity
- Checks whether any human activity is being performed by constantly checking whether the foreground window changed
- Checks adapter addresses which can be used to detect virtual network interfaces
Other Compelling Indicators:
- [FCE] Stops Windows services
- [FCE] Creates a service
- Deletes its original binary from disk
- Sniffs keystrokes
- Installs an hook procedure to monitor for mouse events
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Commonly Used PortConnection ProxyCustom Command and Control ProtocolUncommonly Used Port |
| Credential Access | Credential Dumping |
| Defense Evasion | Disabling Security ToolsFile DeletionHidden Files and DirectoriesHidden WindowProcess InjectionSoftware Packing |
| Discovery | Process DiscoveryVirtualization / Sandbox Evasion |
| Impact | Service Stop |
| Persistence | Hidden Files and Directories |
| Privilege Escalation | Process Injection |
Selection from The Report:
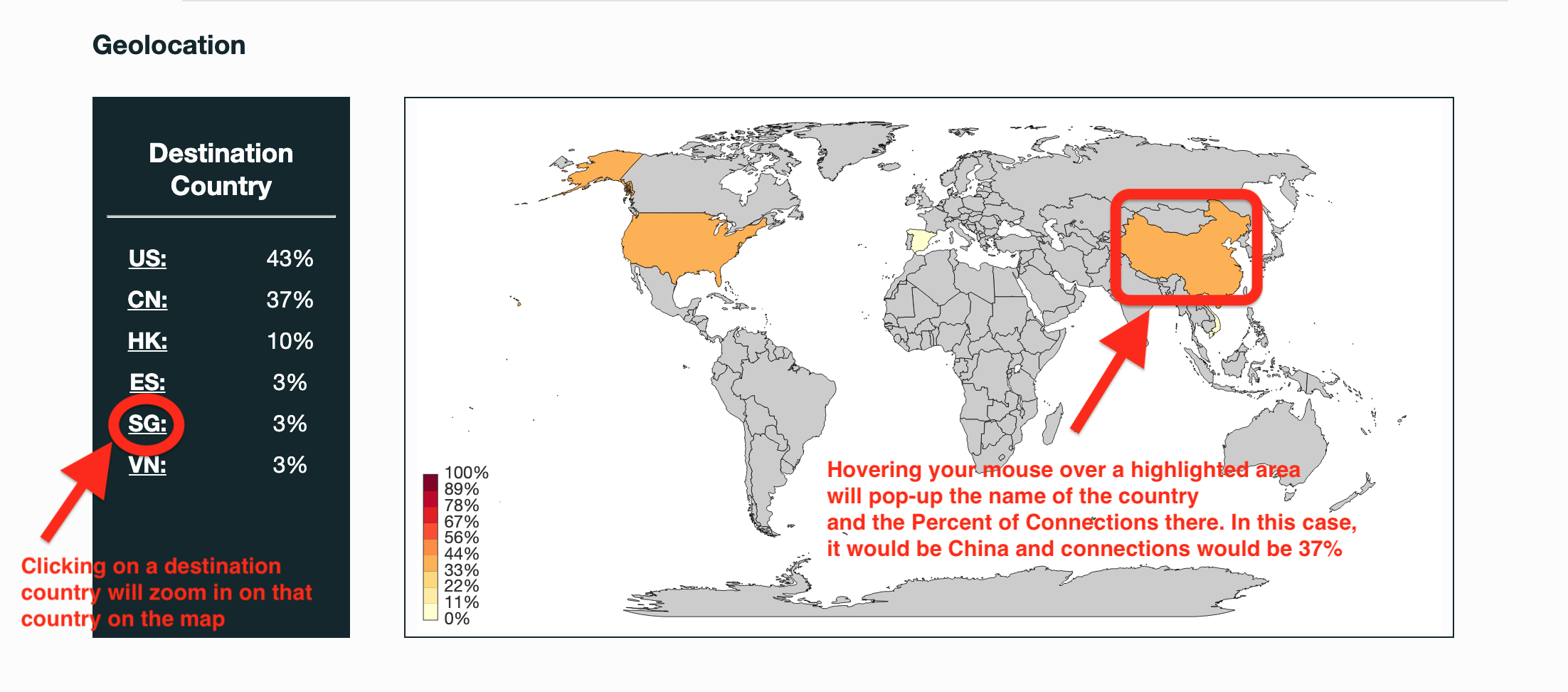
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.