0e46e7cb4bd9cd1a4dcd8b44ce08deba45786c84c54f6e1353fce990c22268ab (SHA-256)
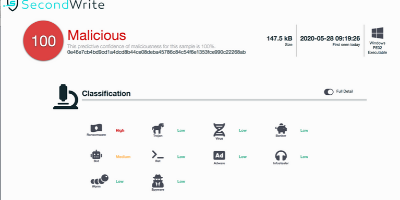
Malicious with 100% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious. unique,
DeepView unique and patented methods – specifically in this case, force code execution and program level indication – identified 7 indicators. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow. Those discovered by DeepView proprietary methods are flagged with [FCE] for forced code execution and [PLI] for program level indication.
Type of Malware: Ransomware
- [FCE] Operates on local firewall’s policies and settings
- [PLI] More than %50 of the external calls do not go through the import address table
- Installs itself for autorun at Windows startup
- Creates an Alternate Data Stream (ADS)
- Attempts to remove evidence of file being downloaded from the Internet
Evasiveness Indicators:
- Attempts to repeatedly call a single API many times in order to delay analysis time
- [FCE] A process attempted to delay the analysis task
- Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available
Other Compelling Indicators:
- [FCE] Connects to an IRC server, possibly part of a botnet
- [FCE] One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
- [FCE] Sample contacts servers at uncommon ports
- [FCE] Creates a hidden or system file
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Uncommonly Used Port |
| Defense Evasion | Disabling Security Tools File Deletion Hidden Files and Directories NTFS File Attributes Software Packing |
| Discovery | Virtualization / Sandbox Evasion |
| Persistence | Hidden Files and Directories Registry Run Keys / Startup Folder |
Selection from The Report:
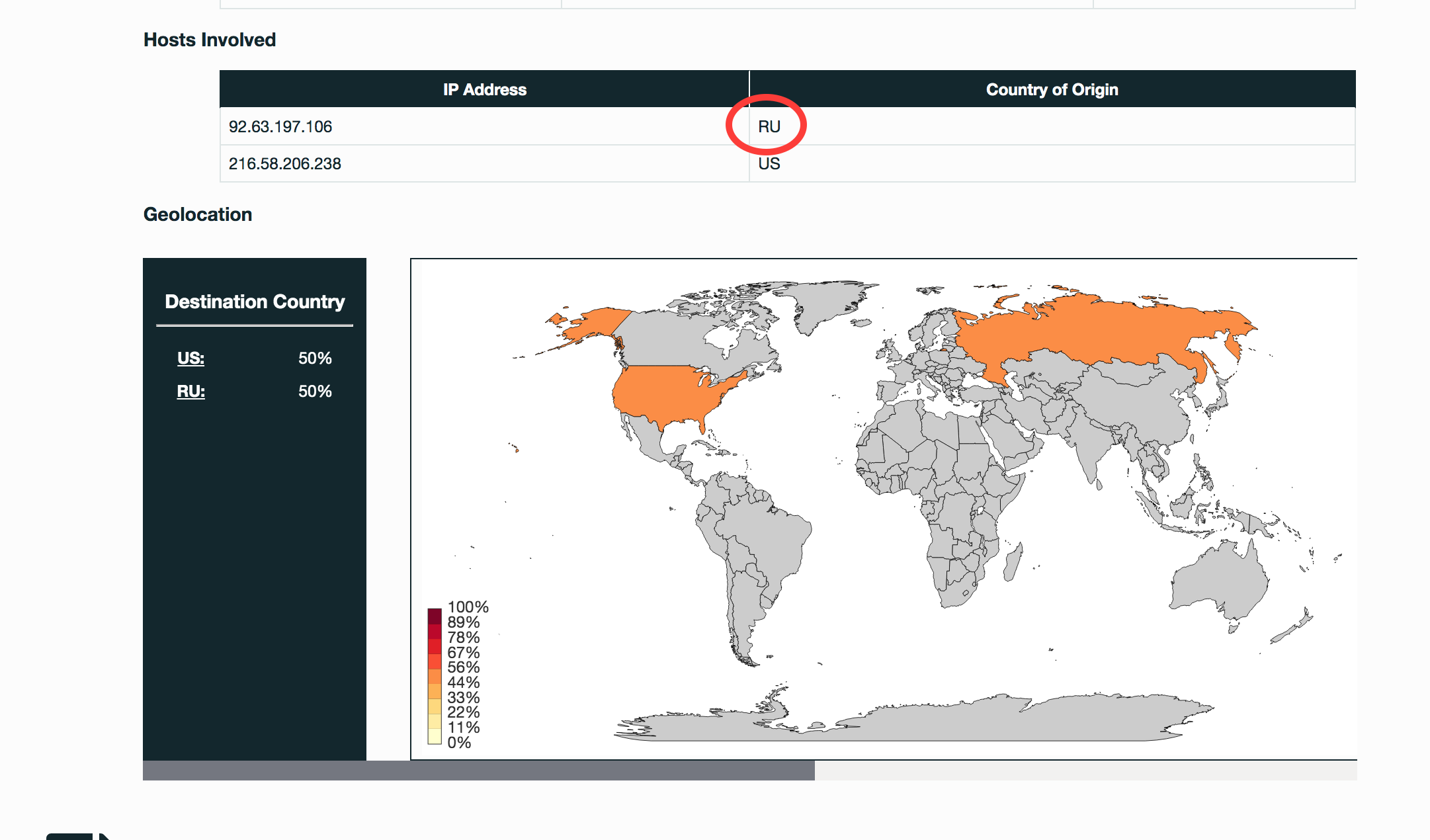
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.