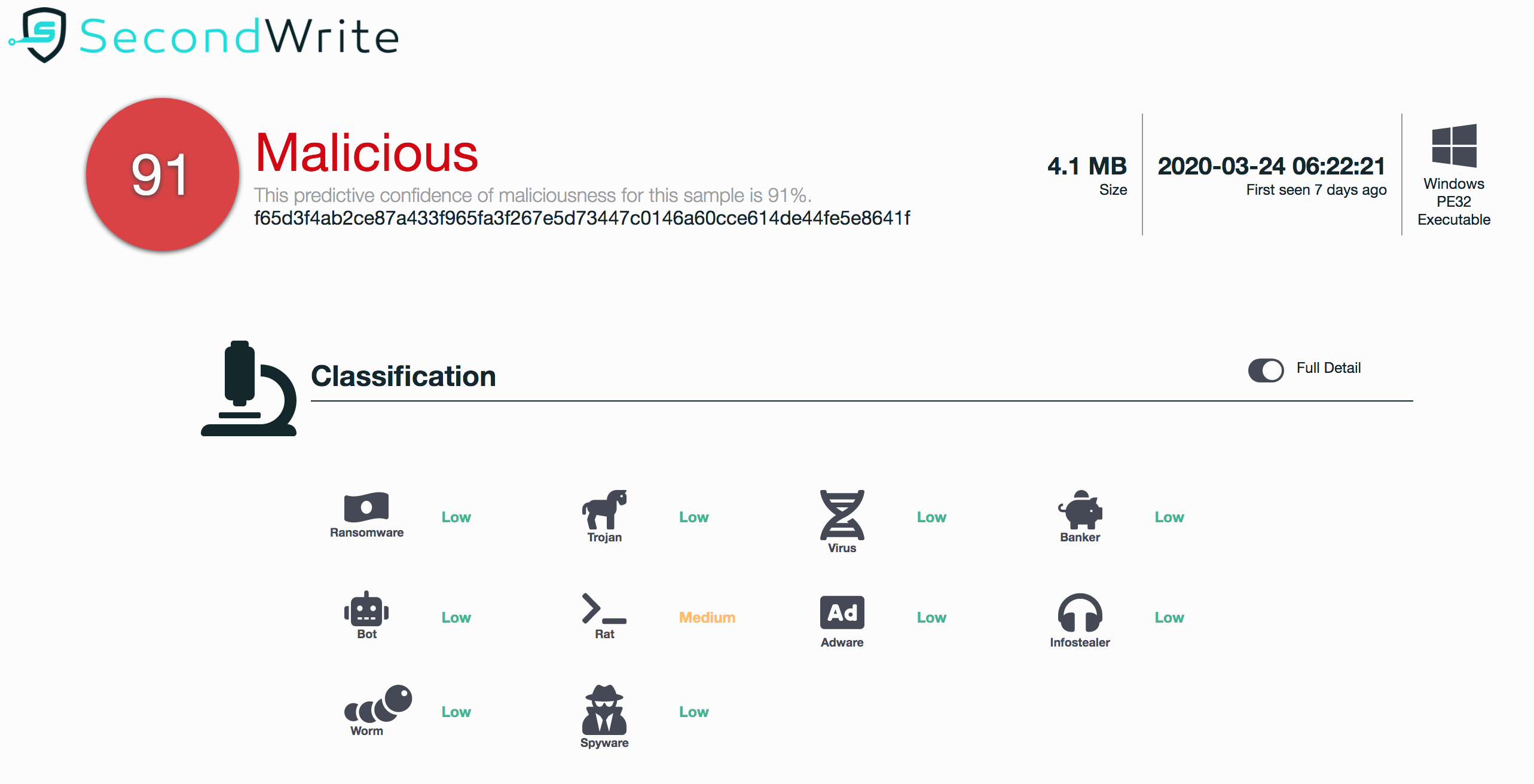
f65d3f4ab2ce87a433f965fa3f267e5d73447c0146a60cce614de44fe5e8641f (SHA-256)
Malicious with 91% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious using our proprietary techniques. At the time of detection, this malware did not appear on leading malware black lists. A link to the full report is below and some key highlights follow:
Type of Malware: RAT
– Creates known Bifrose files, registry keys and/or mutexes
– Drops a binary and executes it
– A process created a hidden window
– Possible date expiration check, exits too soon after checking local time
– Collects information to fingerprint the system (MachineGuid, DigitalProductId, SystemBiosDate)
Evasiveness Indicators:
– Queries information on disks, possibly for anti-virtualization
– Looks for the Windows Idle Time to determine the uptime
– Detects Virtual Machines through their custom firmware
– Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation
– Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available
Other Compelling Indicators:
– Attempts to identify installed AV products by installation directory
– HTTP traffic contains suspicious features which may be indicative of malware related traffic
– One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
– Performs some DNS requests
– Creates executable files on the filesystem
Selection From The Report:
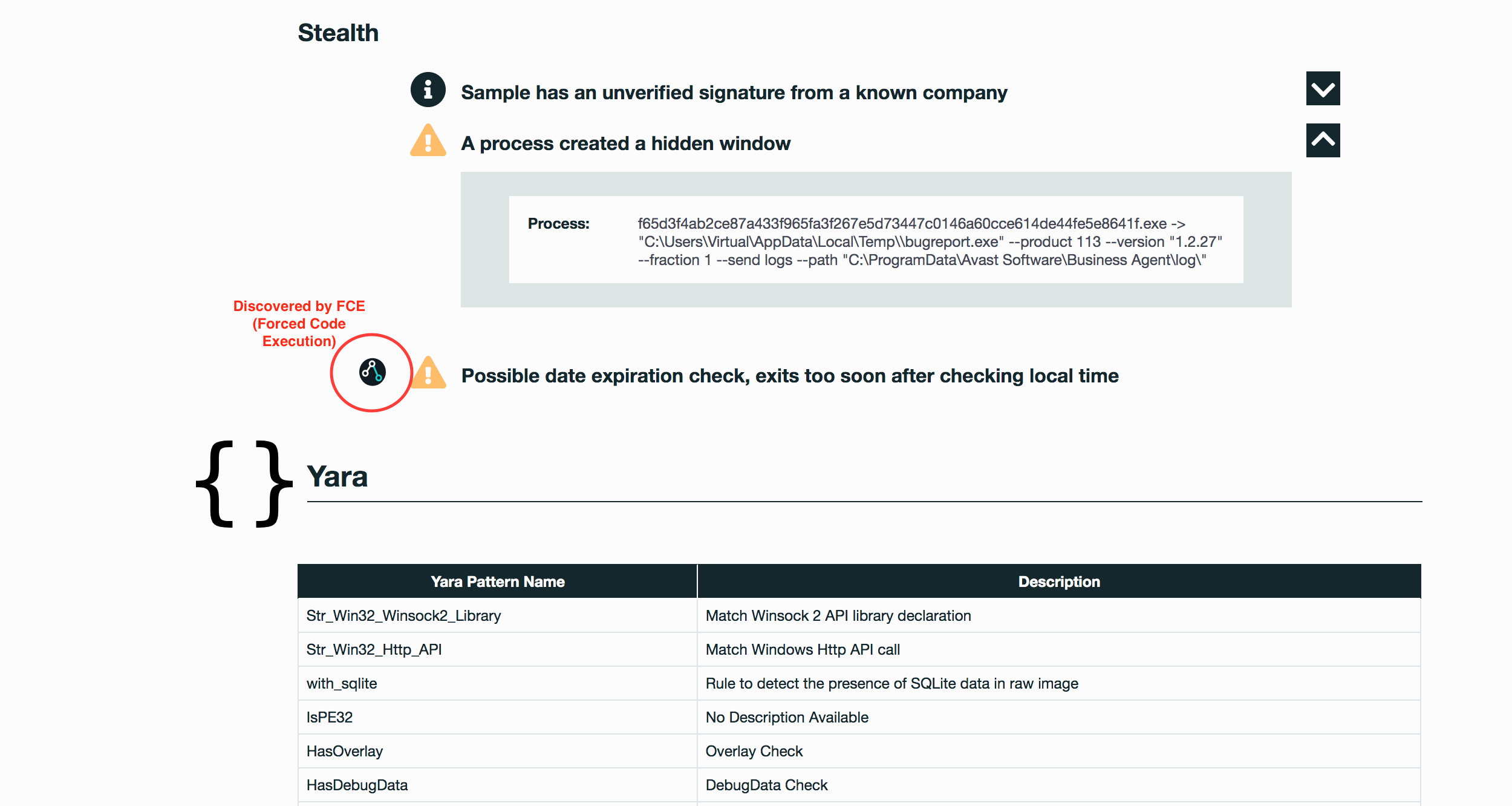
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.