55bc4407a03de9b13654755eea93e5b912fb4754ec0f95381740cb0692807b06 (SHA-256)
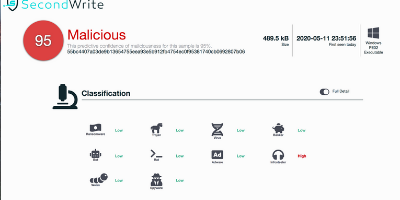
Malicious with 95% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious using our proprietary techniques – which in this case uncovered 5 indicators of significance. At the time of detection, this malware did not appear on any leading malware blacklists. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow:
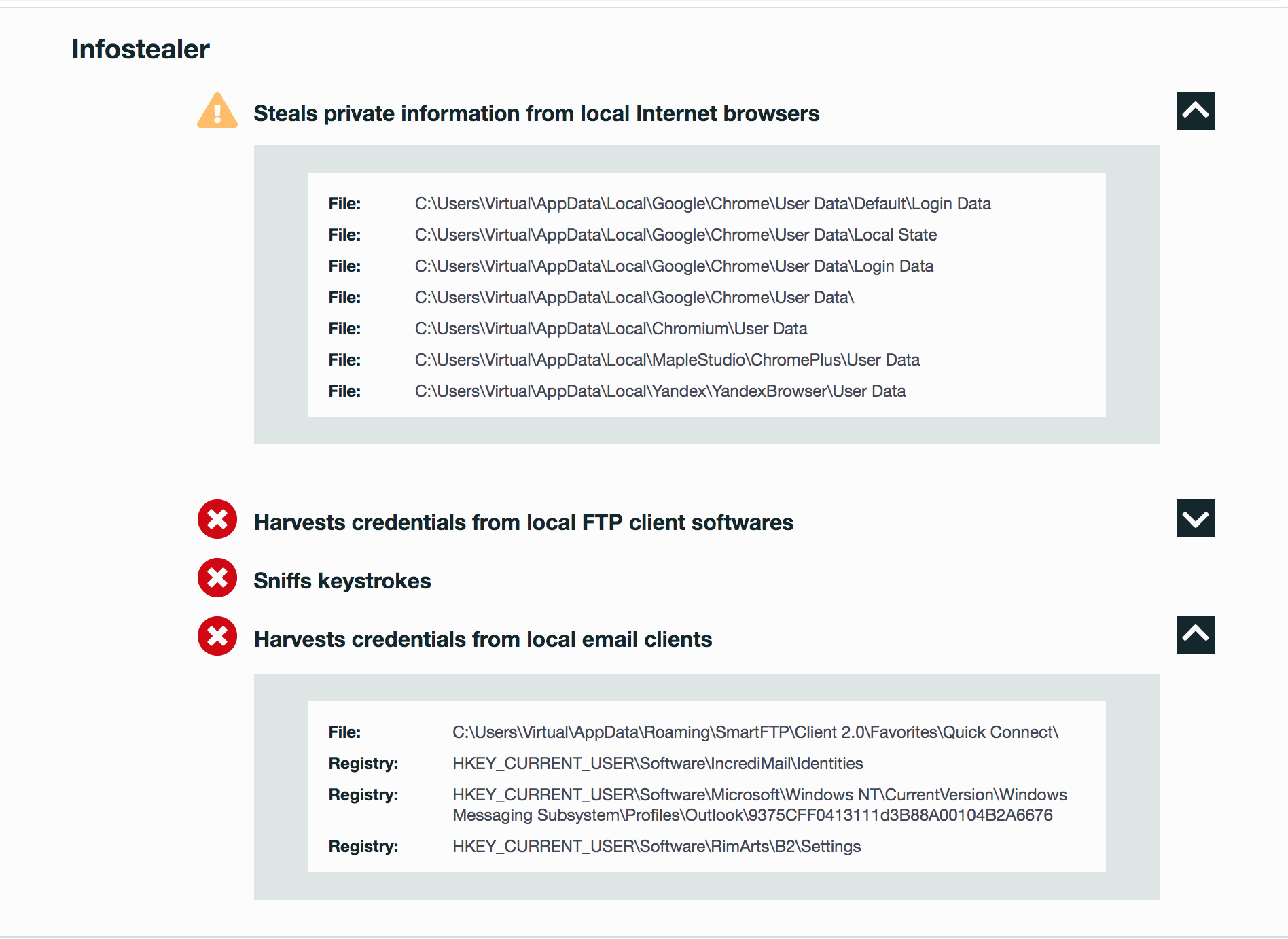
Type of Malware: Infostealer
- Harvests credentials from local email clients
- Sniffs keystrokes
- Harvests credentials from local FTP client softwares
- Steals private information from local Internet browsers
- Creates a windows hook that monitors keyboard input (keylogger)
Evasiveness Indicators:
- Tries to suspend sandbox threads to prevent logging of malicious activity
- Checks adapter addresses which can be used to detect virtual network interfaces
- Attempts to repeatedly call a single API many times in order to delay analysis time
- Looks for the Windows Idle Time to determine the uptime
- Checks the system manufacturer, likely for anti-virtualization
Other Compelling Indicators:
- Strings possibly contain hardcoded IP Addresses
- One or more of the buffers contains an embedded PE file
- One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
- Creates a suspicious process
- Executed a process and injected code into it, probably while unpacking
- Allocates read-write-execute memory (usually to unpack itself)
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Credential Access | Credential Dumping |
| Defense Evasion | Hidden Window Process Injection Software Packing |
| Discovery | Virtualization / Sandbox Evasion |
| Privilege Escalation | Process Injection |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.