036dac6a8b92caca759f4029e2c48c352daf4fbf3297ebf9bb309203c0bbb0f8 (SHA-256)
Malicious with 92% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious using our proprietary techniques. At the time of detection, this malware did not appear on all the leading malware blacklists. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow:
Type of Malware: Infostealer
- Steals private information from local Internet browsers
- Harvests credentials from local email clients
- Strings possibly contain hardcoded IP Addresses
- Creates an Alternate Data Stream (ADS)
- Connects to IP address(es) that are no longer responding to requests (legitimate services will remain up-and-running usually)
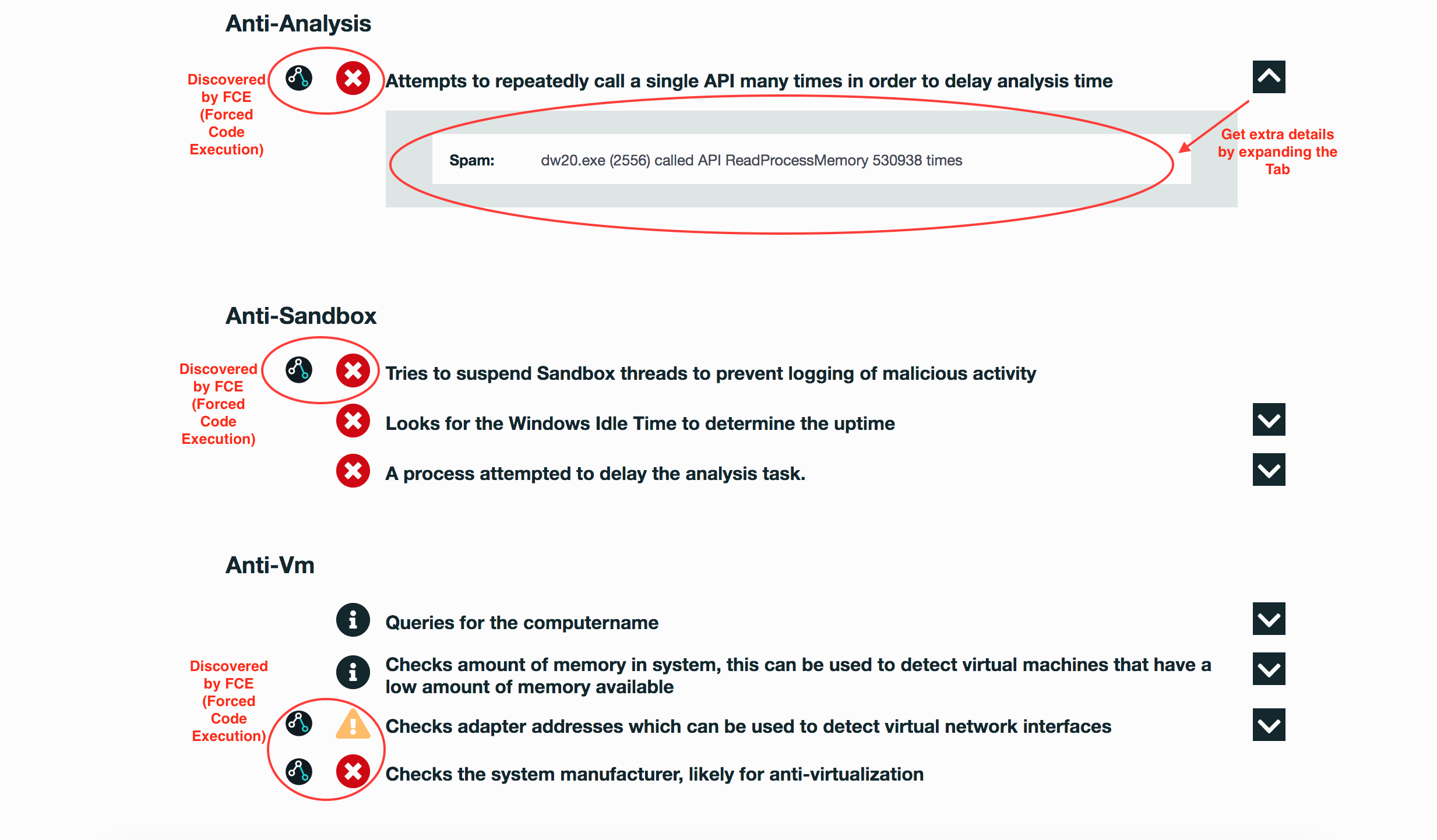
Evasiveness Indicators:
- A process attempted to delay the analysis task
- Looks for the Windows Idle Time to determine the uptime
- Checks the system manufacturer, likely for anti-virtualization
- Checks adapter addresses which can be used to detect virtual network interfaces
- Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory
Other Compelling Indicators:
- Installs itself for autorun at Windows startup
- One or more of the buffers contains an embedded PE file
- Attempts to remove evidence of file being downloaded from the Internet
- One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.
- Strings possibly contain hardcoded IP Addresses
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Credential Access | Credential Dumping |
| Defense Evasion | File Deletion NTFS File Attributes Process Injection Software Packing |
| Discovery | Virtualization / Sandbox Evasion |
| Persistence | Registry Run Keys / Startup Folder |
| Privilege Escalation | Process Injection |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.
