8e9b60a1eaef572e2955edf359350aadea5a86cc122e5d152d094cc6f063edff (SHA-256)
Malicious with 100% Confidence
SecondWrite’s DeepView Sandbox analyzed this file this week and declared it to be malicious.
DeepView unique and patented methods – specifically in this case, force code execution (FCE) and program level indication (PLI) – identified 4 indicators. At the time of its discovery, several market leading malware detection vendors had not identified this file as malicious. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow. Those discovered by DeepView proprietary method are flagged with [FCE] for forced code execution.
Type of Malware: Spyware
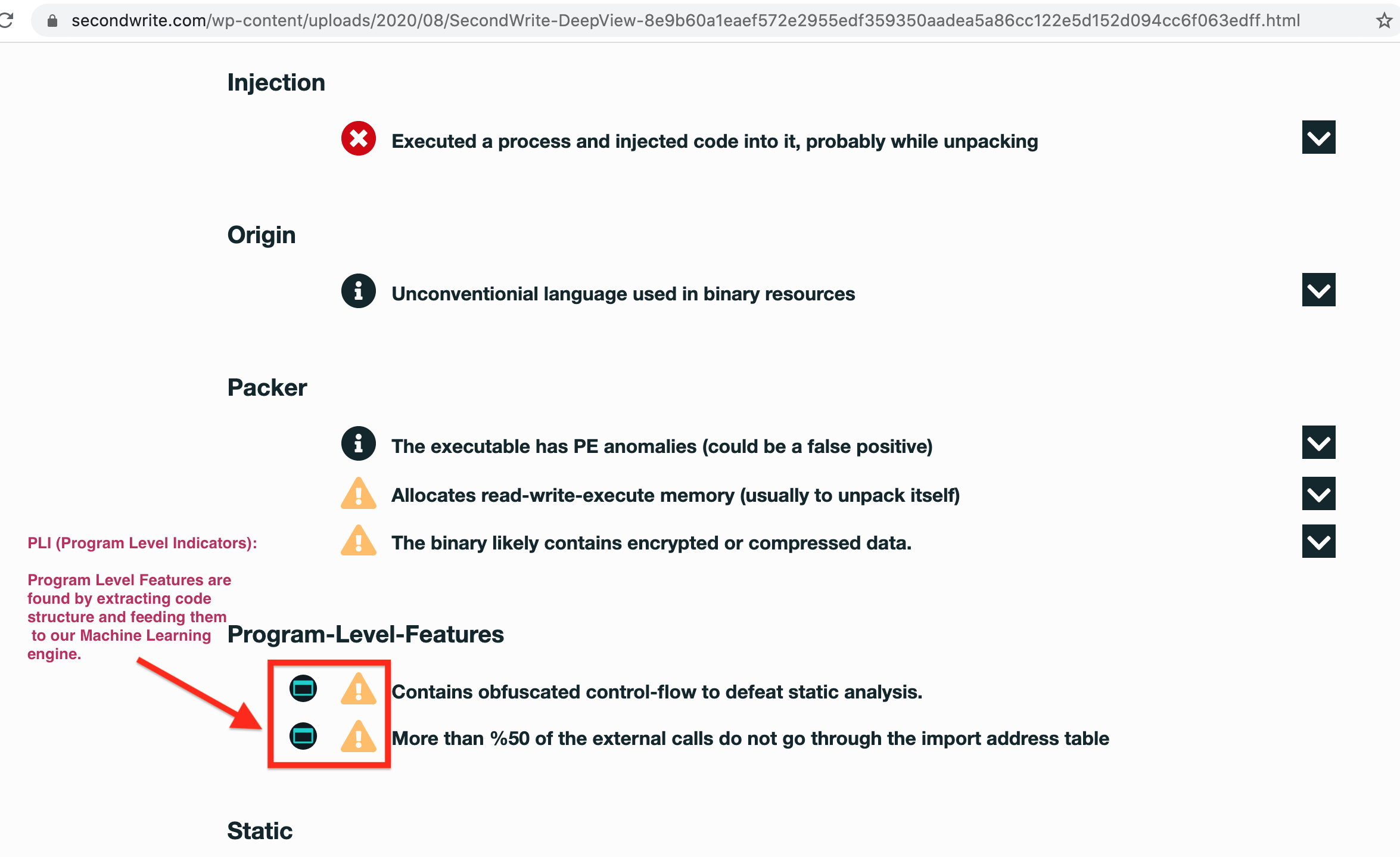
- [PLI] More than %50 of the external calls do not go through the import address table
- [FCE] Repeatedly searches for a not-found process, you may want to run a web browser during analysis
- This sample is detected as: Win.Spyware.Banker-3114
- Presents an Authenticode digital signature
- Unconventional language used in binary resources
Evasiveness Indicators:
- [FCE] Attempts to repeatedly call a single API many times in order to delay analysis time
- [PLI] Contains obfuscated control-flow to defeat static analysis
- Detects Sandboxie through the presence of a library
- Detects VMWare through the in instruction feature
- Checks for the presence of known devices from debuggers and forensic tools
Other Compelling Indicators:
- One or more of the buffers contains an embedded PE file
- The binary likely contains encrypted or compressed data
- Allocates read-write-execute memory (usually to unpack itself)
- Anomalous binary characteristics
- Executed a process and injected code into it, probably while unpacking
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Defense Evasion | Process InjectionSoftware Packing |
| Discovery | Process DiscoverySecurity Software DiscoveryVirtualization / Sandbox Evasion |
| Persistence | Registry Run Keys / Startup Folder |
| Privilege Escalation | Process Injection |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.
