699b599c78d27f4fa580094899974641229f41433514733b1f084e894f28f537 (SHA-256)
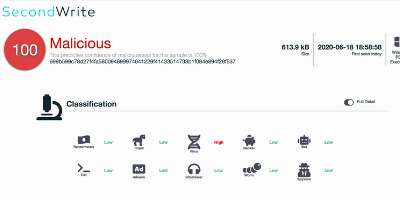
Malicious with 100% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be malicious.
DeepView unique and patented methods – specifically in this case, force code execution and program level indication – identified 1 indicator each. At the time of its discovery, all of the major malware detection vendors had not identified this file of malicious. A link to the full report with descriptions and details is below.
Some key highlights and indicators follow. Those discovered by DeepView proprietary methods are flagged with [FCE] for forced code execution and [PLI] for program level indication.
Type of Malware: Virus
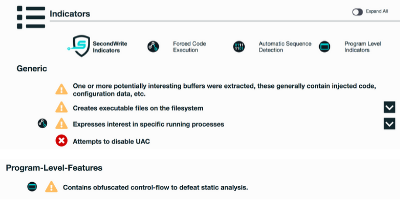
- [FCE] Expresses interest in specific running processes
- Creates a service
- Disables Windows Security features
Evasiveness Indicators:
- A process attempted to delay the analysis task
- [PLI] Contains obfuscated control-flow to defeat static analysis
- Attempts to repeatedly call a single API many times in order to delay analysis time
Other Compelling Indicators:
MITRE ATT&CK Indicators:
| MITRE Tactic | MITRE Technique |
| Command and Control | Commonly Used Port Custom Command and Control Protocol |
| Credential Access | Credential Dumping |
| Defense Evasion | Bypass User Account Control Disabling Security Tools Hidden Files and Directories Hidden Window Software Packing |
| Discovery | Process Discovery Virtualization / Sandbox Evasion |
| Persistence | Hidden Files and Directories Registry Run Keys / Start Up Folder |
Selection from The Report:
See Full Detailed Report:
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection.