d5ffda19d6950757973f52325dbe9b7e01084320e1bdbdcabf9662874d6e6451 (SHA-256)
Malicious with 99% Confidence
SecondWrite’s DeepView Sandbox analyzed this file last week and declared it to be 99% malicious using our proprietary techniques. The full report is below but here are some key highlights
Type of Malware: Infostealer
- Installs a hook procedure to monitor for mouse events
- Sniffs keystrokes
- Queries for the computername
Evasiveness Indicators:
- Attempts to repeatedly call a single API many times in order to delay analysis time
- Checks whether any human activity is being performed by constantly checking whether the foreground window changed
- Tries to suspend Cuckoo threads to prevent logging of malicious activity
- Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation
- Checks adapter addresses which can be used to detect virtual network interfaces
Other Compelling Indicators:
- Attempts to create or modify system certificates
- Drops a binary and executes it
- Attempts to connect to dead IP:Port(s)
- More than %50 of the external calls do not go through the import address table
- Deletes its original binary from disk
Below is a screenshot of a selection from the report. A few of our proprietary techniques are highlighted. A link to the full report follows.
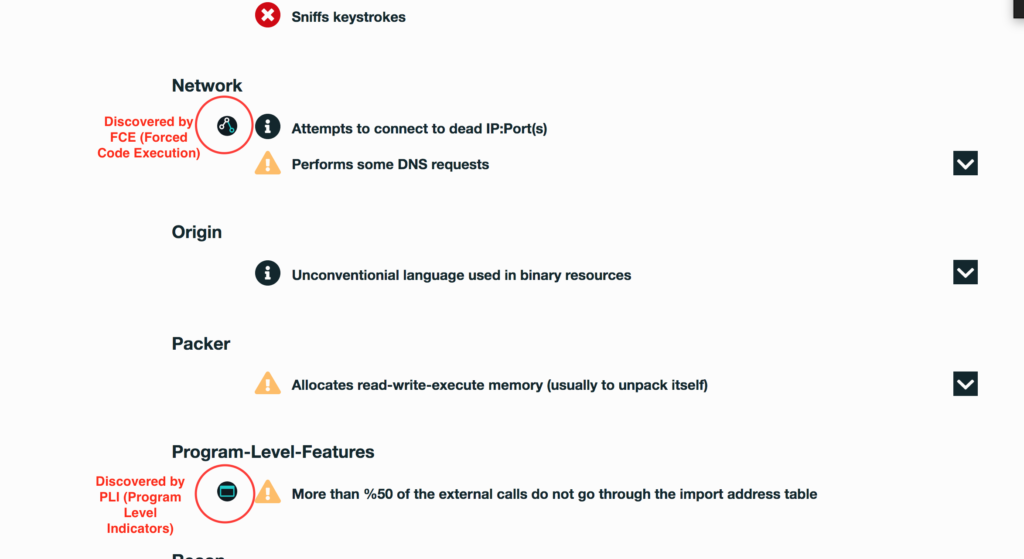
See full detailed report
Malware Of The Week is sourced by DeepView Sandbox using SecondWrite’s patented techniques of Forced Code Execution, Program Level Indicators, and Automatic Sequence Detection
Please email us at info@secondwrite.com to questions about our product
SecondWrite’s malware detection sandbox and threat intelligence products are bringing novel technologies and capabilities to their respective segments for the first time. SecondWrite’s DeepView sandbox product categorizes customer-submitted files as malicious or benign with industry-leading accuracy, and outputs a report detailing the file’s suspicious activity. Unlike competing sandboxes, DeepView forcibly executes hidden malicious paths in the input file, thereby discovering about 50% more Indicators of Compromise (IOCs) than without this technology, and leading to greater detection accuracy.
